Simple and secure data encryption via molecular weight distribution fingerprints†
Abstract
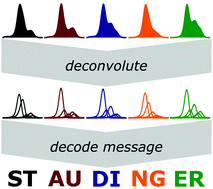
A method for encryption and safe transmission of data in the shape of molecular weight distributions (MWD) is presented. Relatively simple individual distributions serve as the key to encode information by mixing those in known amounts to an overlapped MWD. Increasing molecular weights are used to denote the position of these individual sub-distributions, and the relative quantity per sub-distribution is used to store data. The concept is demonstrated by a series of messages, whereby two-letter codes can be transmitted per overall MWD. In the final step, the encryption safety is confirmed. Due to the inherent differences in SEC calibrations, samples sent from Australia to Belgium could only be deconvoluted when the recipient of the message owned the physical sub-distributions, which then act as the encryption key.


 Please wait while we load your content...
Please wait while we load your content...